Front Page
We have the complete source for total information and resources for Mspy Kurulumu Iphone on the Internet.
It keeps you abreast on who may be grooming your kid or which of them has huge influence on him/her All media sent and received are also monitored. There are two ways you can follow: Go to iforgot.apple.com to access your account with known credentials Reset your password If you tried a few times and did not regain access, try another day. So here are some of the benefits describe under the following heads.
If you're thinking about using mSpy, or if you are currently using it, and have some questions about it, then please read on for an FAQ about mSpy. After that you will see a screen with captcha with a code you need to enter to start downloading process. As previously mentioned, it works in stealth mode. The game also uses cyberbullying as the way to keep children desperate and lead them to suicide. Remotely keep tabs on your kid`s online activities as well as their current GPS location, calls and texts. You can check the websites they see from their tool making sure they're refraining anything that might cause damage to your company's credibility.
Even more Info About Mspy Kurulumu Iphone
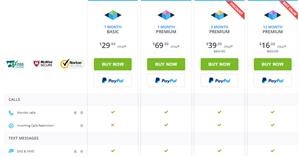
More Resources For Mspy Kurulumu Iphone
However it disappears after the installation process is done. Below you can find the list of features and the price of every package.
Below are Some More Details on Mspy Kurulumu Iphone
When the information is deleted, it is not erased at all until the phone’s memory got it. File explorer helps with unrooting If your device runs Android Lollipop, it’s possible to unroot by removing the files that provided the root. Analytics: Set mSpy to create detailed reports based on pre-selected phone usage and time windows. That is, you're using it as a parent of an underage child, or on a consenting adult.
Below are Some Even more Resources on Mspy Kurulumu Iphone
Parents can not only use basic features like calls, text and GPS monitoring, but also block adult apps and hazardous sites, set safe and dangerous areas, view Wi-Fi hotspots and block the device if it is lost of stolen. Cannot thank enough.” “Why did I decide to use mSpy? This package includes such features: Call history; Contact List; Text Messages; iMessage; WhatsApp; Automatic Updates; Calendar, Notes, Tasks; Installed Applications; Website History; Wi-Fi Networks; 24/7 support. You can view names, numbers – any info input in the phone book. For iPhones, there’s a specific procedure as well. Because of this, we must do everything we can to maintain the requisite security needed to see our businesses flourish and our kids grow up to be happy, healthy and of course, safe young adults.
Previous Next
See Also
Mspy Promo Codes
Mspy Sign In
Mspy Unsichtbar
Terms of Service
Disclosure Statement
DMCA
Privacy Statement
Contact